Introduction
Introduction
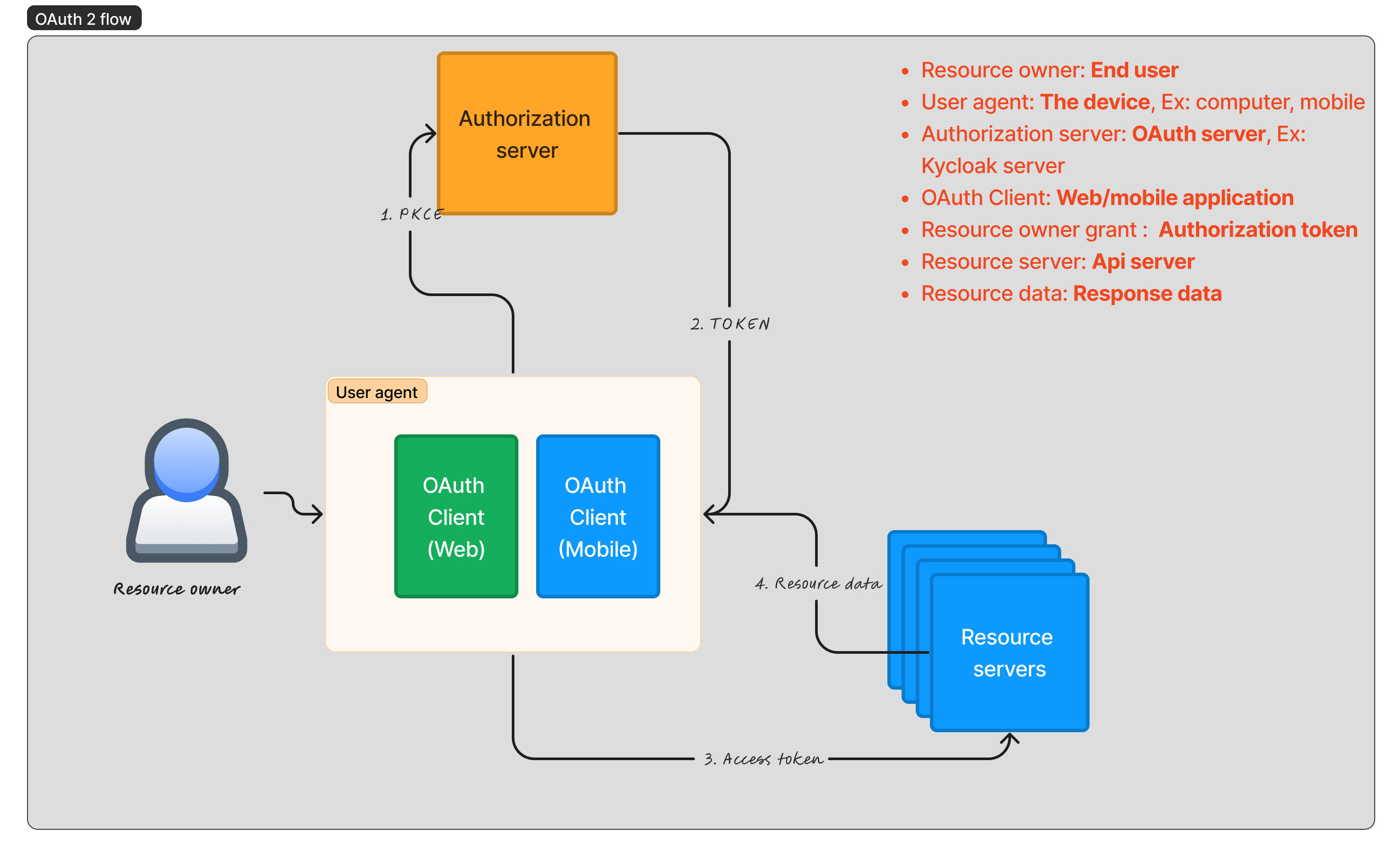
The abbreviation OAuth 2 stands for Open Authorization 2.0, it is is an authorization framework that enables applications to access user data from one service to another without sharing passwords. It grants limited, revocable access tokens, ensuring secure interactions between systems and protecting user credentials.
OAuth 2 is used to enhance security and simplify user authentication for applications and services. It allows apps to access user data without requiring direct access to passwords, reducing the risk of credentials exposure. OAuth 2 also enables controlled access to resources, ensuring better privacy and user control over data sharing.
Authentication?
Identify yourself by providing valid credentials using different medium
Authorization?
Identify yourself by providing valid role that you are eligible to enter or do certain activity.
| No. | Component | Discription | Example |
|---|---|---|---|
| 1 | Resource owner | The user who owns the data or resources | The person |
| 2 | User agent | The software or device used by the user | Web browser, Mobile app |
| 3 | Client | The application requesting access | Social media app, Email client |
| 4 | Authorization server | The server that verifies user identity and issues tokens | Google OAuth server, Facebook OAuth server, Keycloak server |
| 5 | Resource server | Holds the protected user resources | The Api server, |
OAuth client types
OAuth primarily will have two types of clients they are
- Public clients : -- The Mobile apps and single page web applications would come under this category where the secret keys would be exposed publicly
- Private clients : -- The applications that can keep secret access keys safe withouht exposing to publc
Access tokens and formats
access token is generally encrypted text using JWT that created by authorization server when autentication success. The access token may or may not have information related to user when decoded.
The JWT tokens are primarily devided into 3 parts header.payload.signiture, and each part would be seperated by a dot (.), below image explains a sample JWT
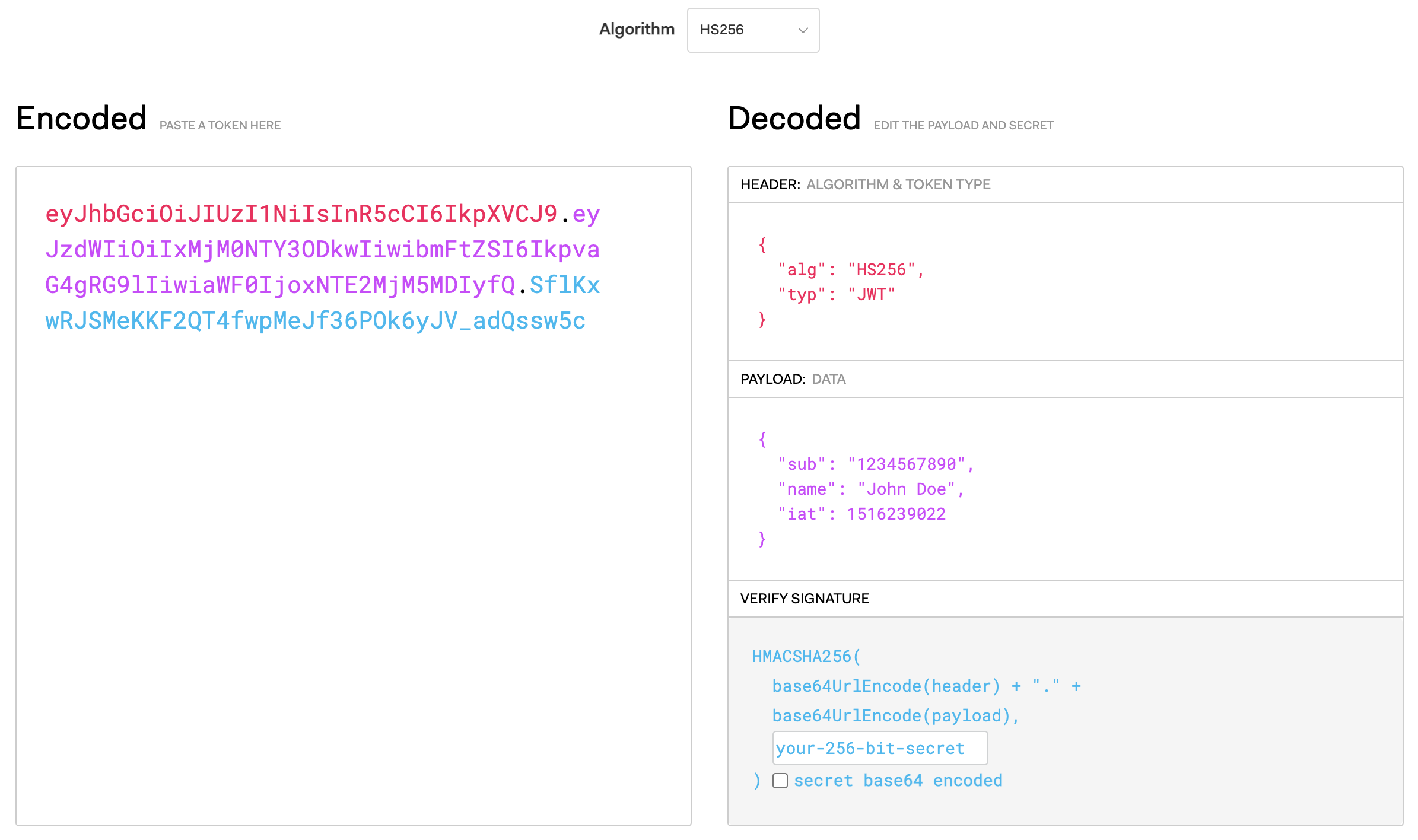
Both the header and payload are simply base64 encoded text which can be decoded easyly to understand the actual text. So it is not recommanded to place any sensitive information in JWT. The signiture play crusial role to make the JWT secure by encrypting the code by choosing a specific algorithms from the supported list of encryptions. more information can be found here https://jwt.io/introduction, and the related RFC documentation also available.
the keys used in JWT header or payload are predefined and called as JWT claims, there can be custom claims based on need. the detailed instrcution of those claimsn can be found here https://www.iana.org/assignments/jwt/jwt.xhtml